Get started on the web platform of your choice
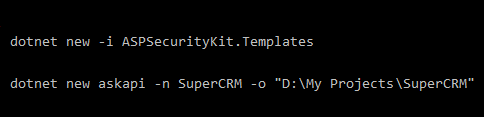
Create the project using the API template
With its interface-driven design, ASK gives you freedom to define data access layer for security the way you want, including repositories and even entity models like User and permit. An implementation as source code is provided via the source packages (an essential one is included within the template).
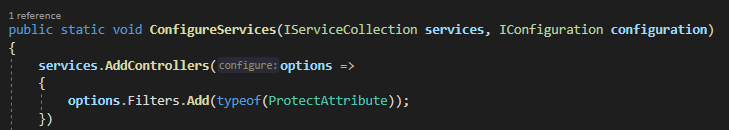
With the Protect filter, you inject the ASK's security pipeline which subjects every incoming request to every action of your web app to a range of security checks.
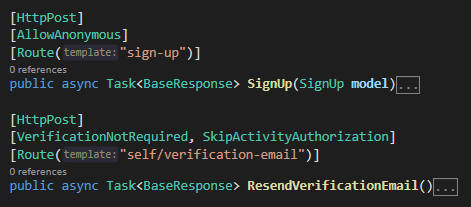
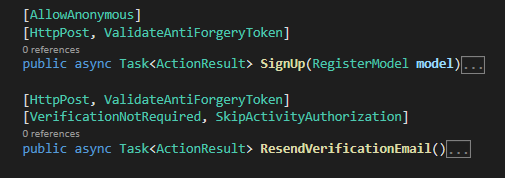
The pipeline's Zero Trust nature requires that you explicitly opt-out actions from checks you don't need. For example, here using AllowAnonymous, VerificationNotRequired and SkipActivityAuthorization attributes to opt out of authentication, verification and activity authorization checks, respectively:
The activity data authorization (ADA) gives you a convention-based approach to authorize actions and the data sent for those actions, without writing any code in most cases:
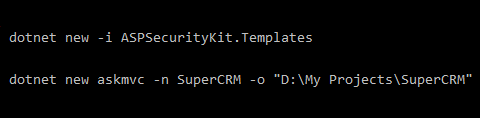
Create the project using the MVC template
With its interface-driven design, ASK gives you freedom to define data access layer for security the way you want, including repositories and even entity models like User and Permit. An implementation as source code is provided via the source packages (an essential one is included within the template).
With the Protect filter, you inject the ASK's security pipeline which subjects every incoming request to every action of your web app to a range of security checks.
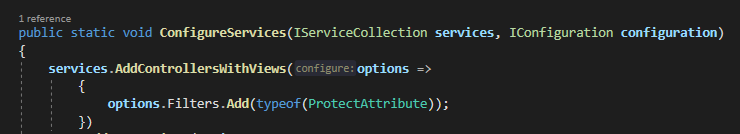
The pipeline's Zero Trust nature requires that you explicitly opt-out actions from checks you don't need. For example, here using AllowAnonymous, VerificationNotRequired and SkipActivityAuthorization attributes to opt out of authentication, verification and activity authorization checks, respectively:
The activity data authorization (ADA) gives you a convention-based approach to authorize actions and the data sent for those actions, without writing any code in most cases:
Create the project using the ServiceStack template
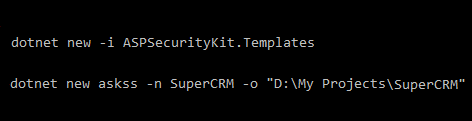
With its interface-driven design, ASK gives you freedom to define data access layer for security the way you want, including repositories and even entity models like User and Permit. An implementation as source code is provided via the source packages (an essential one is included within the template).
With the ASPSecurityKitFeature (a ServiceStack plugin), you inject the ASK's security pipeline which subjects every incoming request to every operation of your web app to a range of security checks.
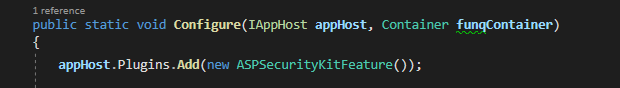
The pipeline's Zero Trust nature requires that you explicitly opt-out operations from checks you don't need. For example, here using AllowAnonymous, VerificationNotRequired and SkipActivityAuthorization attributes to opt out of authentication, verification and activity authorization checks, respectively:
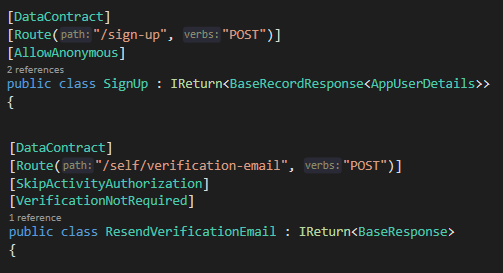
The activity data authorization (ADA) gives you a convention-based approach to authorize operations and the data sent for those operations, without writing any code in most cases:
Protect your server application
with a comprehensive security pipeline
built on Zero Trust model
Multiple stages of checks and verifications with events, hooks & settings to alter the existing and inject custom checks at any stage
Cross-Site Scripting (XSS)
Detect/resist XSS injections and holistically sanitize data across various subsystems (emails, APIs, back-end/front-end).
Authentication
Allow multitude of clients (browsers, mobile apps, IoT devices, backend jobs, third-party services) to connect securely using schemes like HMAC, cookies, service key and identities such as site keys, feature keys and sessions.
IP Firewall
Restrict access to only secure networks or machines for not just automated API key based calls, but for any identity (including user sessions, to protect high-privileged user accounts).
Multi-Factor Auth (MFA)
Protect user accounts with MFA (2FA) checks – enforce MFA as a policy on users, opt out specific users, operations or networks from MFA verification.
User Account Verification
Limit access to the system until user's contact details (such as email/mobile) are verified. Opt out certain operations (such as user profile) from verification check. Get end-to-end implementation of email verification workflow.
Activity-Data Authorization (ADA)
Authorize callers for not just actions but also for the data on which actions are being performed, with a convention-based ADA component that automatically determines permissionCodes and discovers sensitive data fields in requests, and gives you various options to override the default conventions.
Suspension
Suspend not just users but operations on all kinds of entities – such as financial accounts, contacts, etc. for reasons such as KYC required, fraud detected, OFAC. Allow certain operations on suspended entities such as read-only access, upload KYC document.
"BHIS would like to commend Forge Trust on their implementation of the authorization header. The dynamic nature of this header helps to secure the application by preventing replay attacks and request tampering."
Cut cost, ship fast
ASPSecurityKit cuts the time it takes to develop secure web applications and APIs by 20%.
Without writing a single line of code, get implementation of several important common workflows including,
- Account management (register, login, two-factor auth, forgot password, account settings, IP firewall management, email verification)
- User management (add/remove/suspend users, permissions)
- Administration (impersonation, transfer)
- Security event notifications
- Production-ready error handling
and much more, right into your project as source code – models, views, controllers or API endpoints with best practices (async, managers, dependency injection, error handling)!
"ASPSecurityKit has saved us hundreds of developer hours and thousands of Pounds. I was blown away by the speed at which our developer single-handedly developed a complex multi-tenanted, multi-user order lifecycle management web application for a prestigious client in record time."
Create marketplace systems
(connecting buyers / sellers)
or hierarchical systems
(as in an organization chart)
or a mix of these with ease.
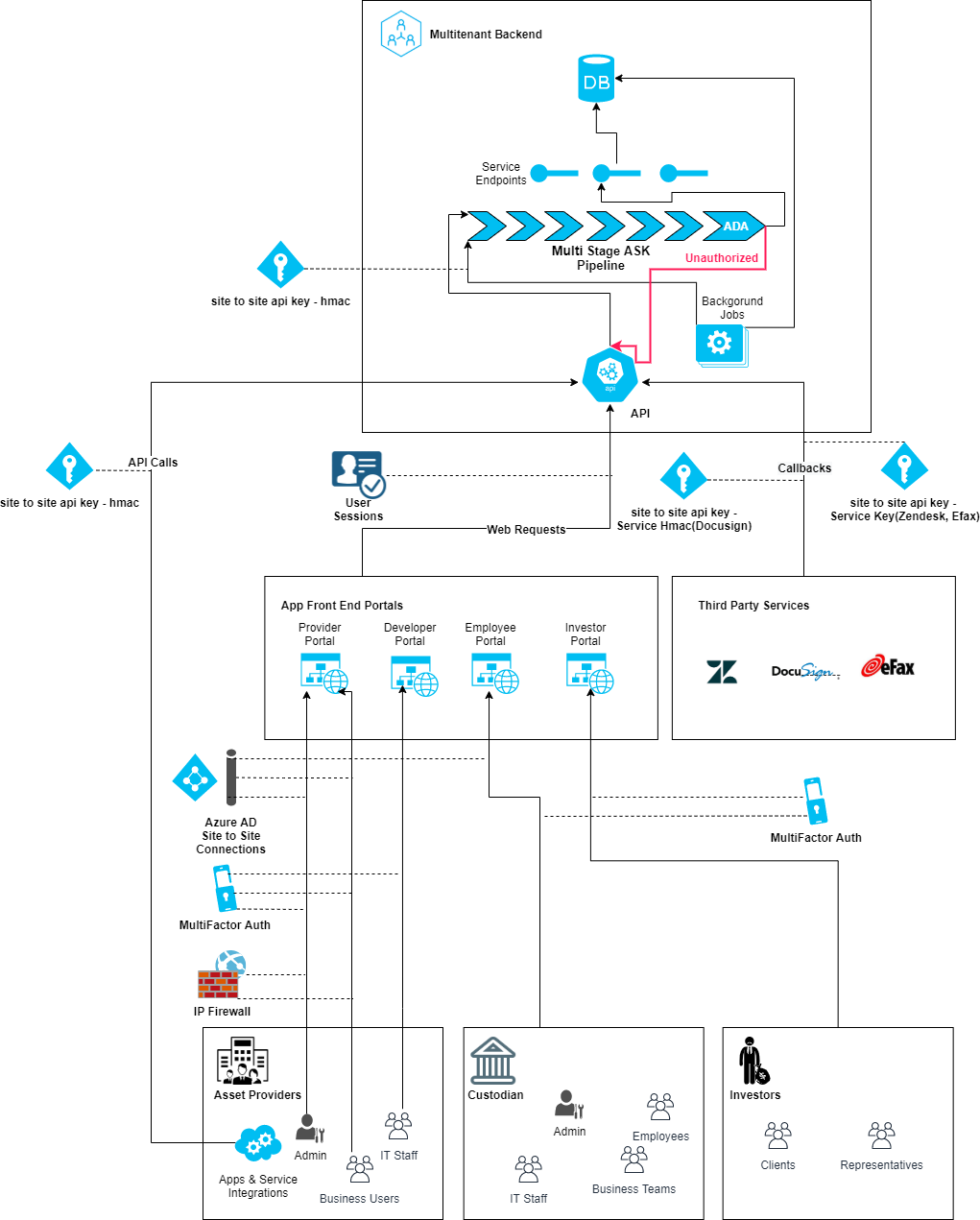
Financial System
- Above architecture represents an IRA custodian cloud system like ISCP that has multiple institutional tenants in form of asset providers, individual IRA clients and a custodian. Both providers and custodian have multiple kinds of users representing various business roles.
- XSS, MFA, IP Firewall, ADA are the various checks enforced by the ASPSecurityKit's multi-stage security pipeline.
- HMAC, ServiceKey, ServiceHMAC, AuthCookie are the authentication schemes supporting different integration scenarios with client apps/third-party services, referring identities such as user sessions, site-to-site API keys to authenticate.
- ADA is a unique access control mechanism that gives you convention-based, granular control on what operations a caller can execute and on what data it can execute those operations.
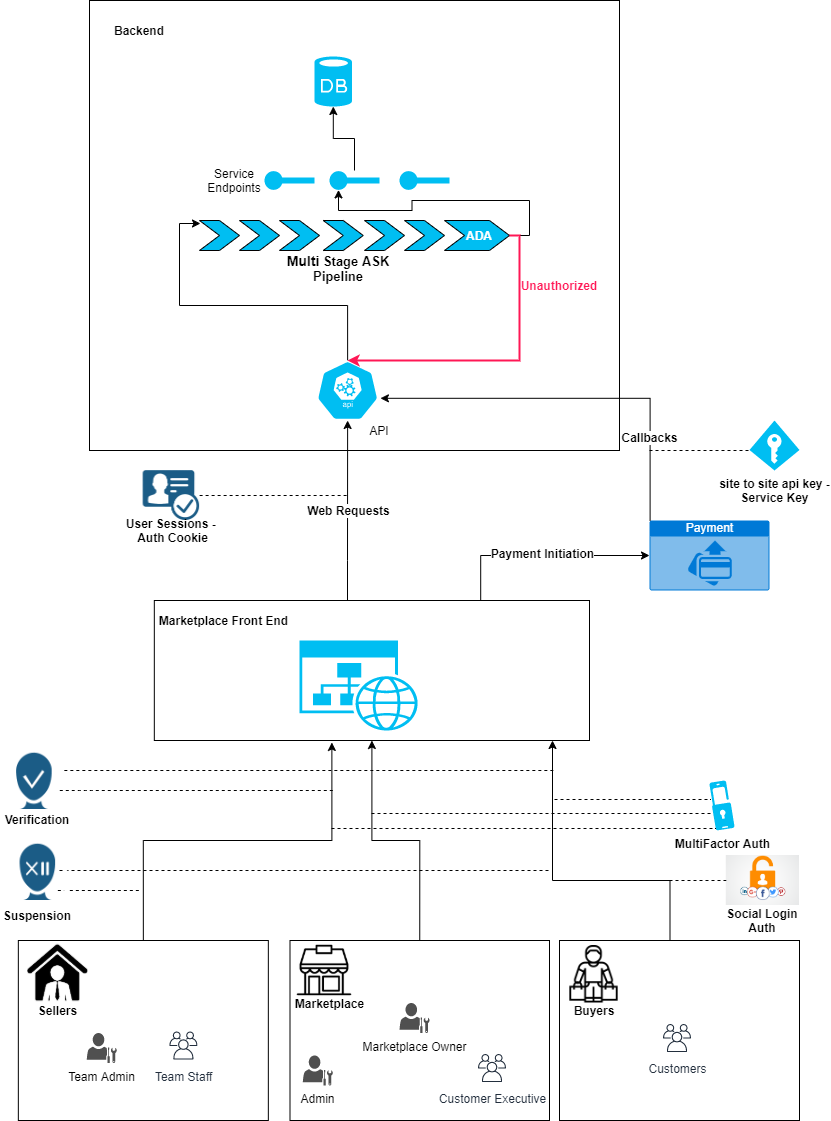
Marketplace System
- Above architecture represents an ECommerce marketplace cloud system that has multiple institutional tenants in form of sellers, individual/institutional buyers and the ECommerce company. The institutional clients and ECommerce company have multiple kinds of users representing various business roles.
- XSS, MFA, Suspension, Verification, ADA are the various checks enforced by the ASPSecurityKit's multi-stage security pipeline.
- HMAC, ServiceKey, AuthCookie are the authentication schemes supporting different integration scenarios with client apps/third-party services, referring identities such as user sessions, site-to-site API keys to authenticate.
- ADA is a unique access control mechanism that gives you convention-based, granular control on what operations a caller can execute and on what data it can execute those operations.
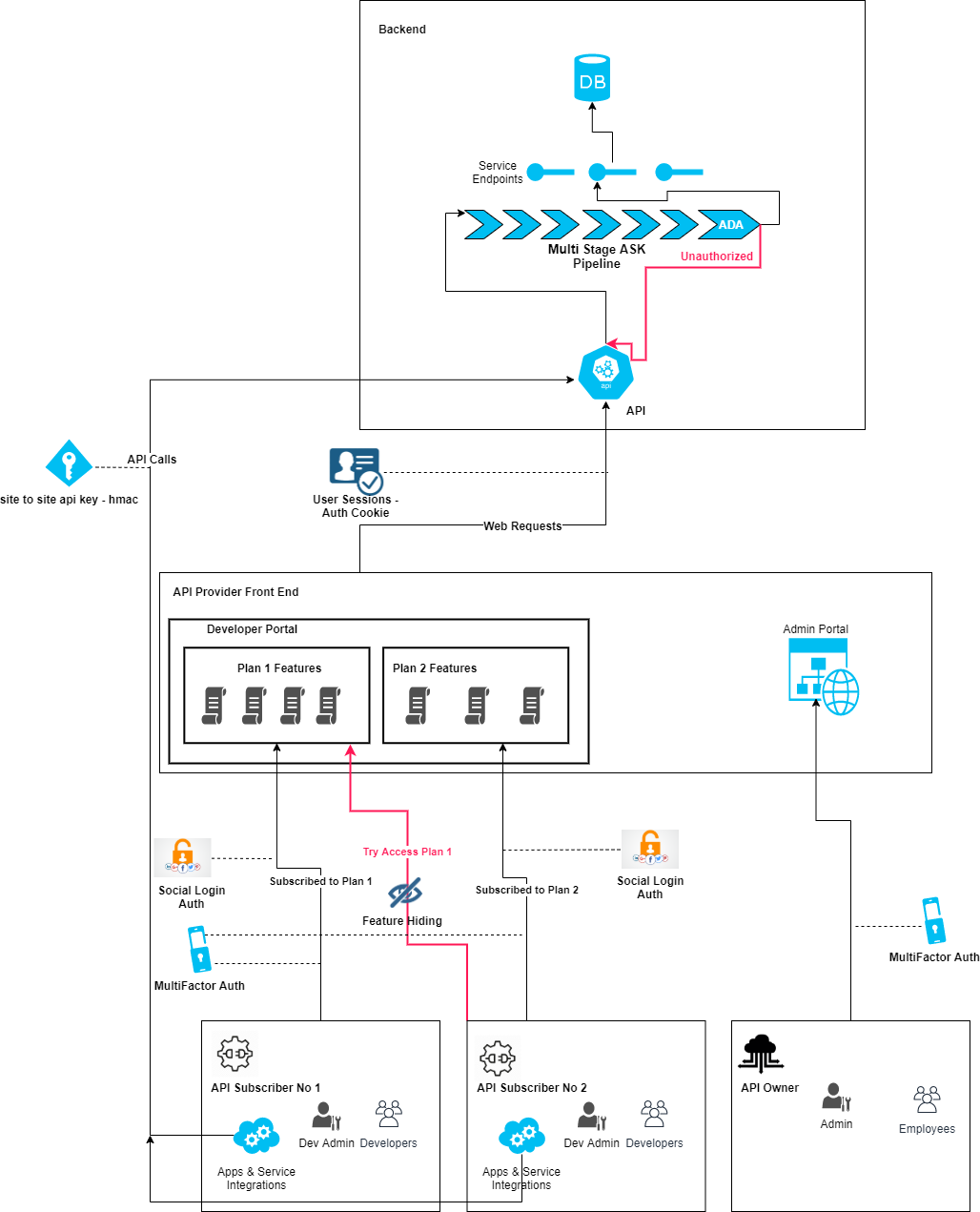
Developer Portal
- Above architecture represents a developer portal supporting different grades of API subscriptions, giving access to only the portion of docs included within the subscribed plan, made possible by the granularity of ASK's ADA feature.
- XSS, MFA, ADA are the various checks enforced by the ASPSecurityKit's multi-stage security pipeline.
- HMAC, AuthCookie are the authentication schemes supporting different integration scenarios with client apps/third-party services, referring identities such as user sessions, site-to-site API keys to authenticate.
- ADA is a unique access control mechanism that gives you convention-based, granular control on what operations a caller can execute and on what data it can execute those operations.
Protect against today's threat landscape;
harden against OWASP Top Ten
and be prepared against evolving future threats with regular library updates and expert guidance
ASPSecurityKit is,
an outcome of a decade of experience in developing security features in projects for clients ranging from multi-billion financial institutions, private healthcare, insurance, to hospitality, manufacturing, classified crypto marketplaces and customer support services.
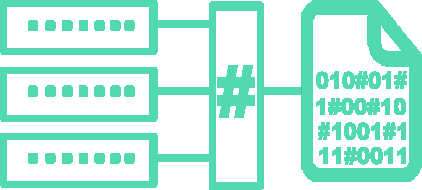
 Password hashing using PBK salted hashing protecting against dictionary attacks.
Change the default hashing algorithm with ease
Password hashing using PBK salted hashing protecting against dictionary attacks.
Change the default hashing algorithm with ease